How Hashing & Salting make any password secure with Blockchain ?
What is Hashing?
- Dictionary Attacks

- Brute Force Attacks
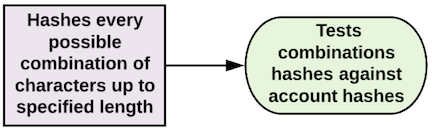
- Lookup Tables
- Reverse Lookup Tables
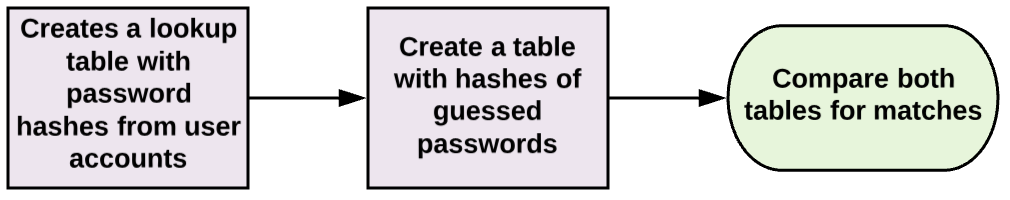
*Note the difference between lookup tables and reverse lookup tables. Lookup tables begin with the precomputed password guess hashes, while reverse lookup tables begin with the table of password hashes from the user accounts database.
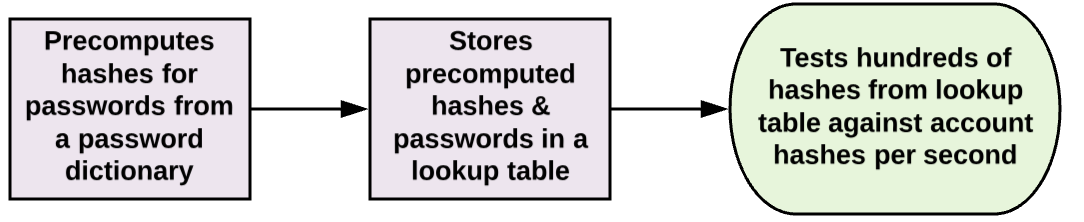
- Rainbow Tables
Rainbow tables are very similar to reverse lookup tables, except rainbow tables use reduction functions to make significantly smaller lookup tables. The result is a trade-off, where rainbow tables are slower, but require less storage space.
In order to add an additional layer of security, randomness needs to be added to the original plaintext value before hashing so that it will not generate the same hashed value each time. Randomizing these hashes by appending or prepending a random string, known as a salt, can make it significantly more challenging for an attacker to use lookup tables or rainbow tables to crack these passwords by increasing the possible hashed values each password can have. If each user has a unique salt, that makes the password immune against reverse lookups too. An internal file system which has hashed passwords with a salt would look as follows –
hash (“letmein” + “F34564R8”) = 8f3k9j3hdk98jk30lsvn9al30lfb48slhbtwe9uka903bwj380dsfj3v2nf930nk3
hash (“letmein” + “Y456f3q9”) = ber5jg0qhekgl8dkjhl52309uwlkmcbkuw385b9smqnv9c234calq95nf34flql
hash (“letmein” + “56hwF3h8”) = w2lkg034fmwprm80n59fdmal40djwbel46n32ldn2la9702nd772ha95lg06j
Now, for each user with the password “letmein” there is a different hashed value.




Nice Information (Y)
ReplyDelete